
A security report has been published on a set of 56 vulnerabilities that are collectively called Icefall and affect operational technology (OT) equipment used in various critical infrastructure environments.
The Icefall collection has been discovered by security researchers at Forescout’s Vedere Labs and it impacts devices from ten vendors. The type of security flaws included allow remote code execution, compromising credentials, firmware and configuration changes, authentication bypass, and logic manipulation.
Affected vendors count Honeywell, Motorola, Omron, Siemens, Emerson, JTEKT, Bentley Nevada, Phoenix Contract, ProConOS, and Yokogawa. They have been notified in a responsible disclosure coordinated by Phoenix Contact, CERT VDE, and the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
Over the past few years, the type of systems impacted by Icefall has become a more frequent target of specialized malware Industroyer 2 and CaddyWiper, both deployed not to long ago by Russian hackers against Ukrainian power plants.
Overview of vulnerabilities
The flaws discovered by Vedere Labs concern primarily credential security, firmware manipulation, and remote code execution, while manipulating configuration and creating a denial-of-service (DoS) state account for a lower number.
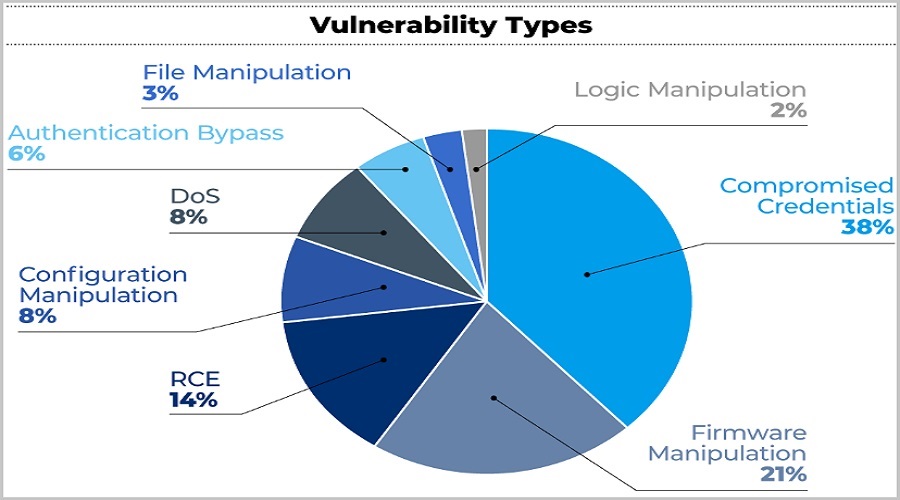
Forescout notes in its report that “many vulnerabilities are due to the insecure-by-design nature of OTs,” also adding that “many authentication schemes are broken,” which shows insufficient security controls in the implementation stage.
As an example, the researchers point out that many devices used plaintext credentials, weak or broken cryptography, hardcoded keys, and client-side authentication.
These authentication flaws pave the way for threat actors to achieve remote code execution (RCE) and DoS condition, or install malicious firmware images. Direct operational manipulation by issuing commands on the target devices or those behind them is another risk that the researchers highlight.
Potential consequences
Icefall impacts a wide range of devices used in numerous industrial sectors, making them highly attractive especially to state-sponsored adversaries.
Some scenarios that Forescout says could stem from threat actors leveraging Icefall include creating false alarms, changing flow setpoints, disrupting SCADA operations, or disabling emergency shutdown and fire safety systems.
To demonstrate their findings and the risk potential, the researchers used a wind power generation and a natural gas transport system, showing where the various Icefall flaws are located and how they could be chained to achieve deeper levels of compromise.
Affected devices are dispersed across the world. The analysts used Shodan to scan the internet for exposed vulnerable systems and found the following top six:
- Honeywell Saia Burgess – 2924 devices across Italy, Germany, Switzerland, Sweden, and France.
- Omron controllers – 1305 devices across Spain, Canada, France, US, and Hungary.
- Phoenix Contact DDI – 705 devices across Italy, Germany, India, Spain, and Turkey.
- ProConOS SOCOMM – 236 devices across China, the US, Germany, Singapore, and Hong Kong.
- Honeywell Trend Controls – 162 devices across France, Denmark, Italy, Spain, and the UK.
- Emerson Fanuc /PACSystems – 60 devices across the US, Canada, Poland, Taiwan, and Spain.
Notably, 74% of the vulnerable product families had been certified for their security, which reflects that these procedures are neither foolproof nor comprehensive enough.
Mitigation possibilities
The primary security recommendation is to apply the latest firmware updates from the vendor. At this time, though, not all of the mentioned vendors have released fixes for Icefall and there are also downstream vendors that need to take action.
Until a fix becomes available or can be installed, system administrators are strongly advised to segment the network and monitor traffic and device activity.
Discovering and replacing vulnerable products with “secure-by-design” devices as well as installing physical switches are good methods to lower the change of a compromise.
Forescout found the Icefall set of vulnerabilities through in-depth manual and automated analysis of the software, firmware and hardware components. The company has published a more detailed technical report, describing all but four vulnerabilities that affect one vendor, which are still under disclosure.
Companies are advised to follow the security advisories from each vendor to learn more details about the specific impact each vulnerability has on an affected product.
Source: www.bleepingcomputer.com
















