A ransomware threat called HardBit has moved to version 2.0 and its operators are trying to negotiate a ransom payment that would be covered by the victim’s insurance company.
Specifically, the threat actor tries to convince the victim that it is in their interest to disclose all insurance details so they can adjust their demands so the insurer would cover all costs.
Emergence of HardBit 2.0
The first version of HardBit was observed in October 2022, while version 2.0 was introduced in November 2022 and it is still the currently circulating variant, according to a report from Varonis, a data security and analytics company.
Unlike most ransomware operations, HardBit does not feature a data leak site, although its operators claim to steal victim data and threaten to leak it unless a ransom is paid.
As a ransomware strain, HardBit 2.0 features some capabilities to lower the victim’s security, like modifying the Registry to disable Windows Defender’s real-time behavioral monitoring, process scanning, and on-access file protections.
The malware also targets 86 processes for termination, to make sensitive files available for encryption. It establish persistence by adding itself to the “Startup” folder, and deletes the Volume Shadow copies to make data recovery more difficult.
An interesting element concerning the encryption phase is that instead of writing encrypted data to file copies and deleting the originals like many strains do, HardBit 2.0 opens the files and overwrites their content with encrypted data.
This approach makes it harder for experts to recover the original files and makes the encryption slightly faster.
Ransom negotiation
Like other ransomware strains, the note that HardBit 2.0 drops on the victim’s system does not inform of the amount the hackers want in exchange for the decryption key. Victims get 48 hours to contact the attacker over an open-source encrypted peer-to-peer communications messaging app.
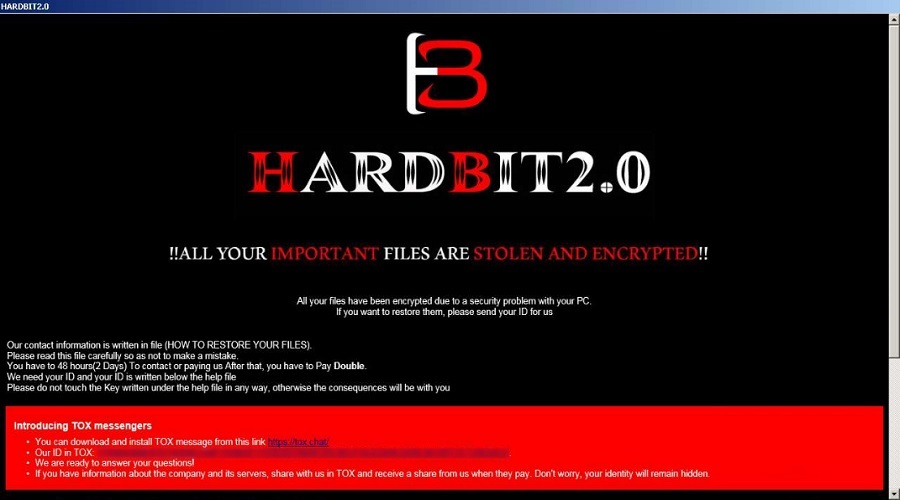
The threat actor advises the victims not to work with intermediaries, since this would only drive up the total cost, but to contact them directly for negotiations.
For companies that have insurance for cyberattacks, the hackers have a more elaborate set of instructions and urge them to disclose the insurance amount for successful dialogue.
Even more, the hackers make it look like sharing the insurance details is beneficial to the victim, painting the insurer as the bad guy that stands in the way of recovering their data.
The threat actors say that insurers never negotiate with ransomware actors with their client’s interests in mind, so they make ludicrous counter-offers to their demands just to derail the negotiations and refuse to pay.
“To avoid all this and get the money on the insurance, be sure to inform us anonymously about the availability and terms of the insurance coverage, it benefits both you and us, but it does not benefit the insurance company,” HardBit operators say in a note to victims.
The attackers say that if they know the exact insurance amount, they would know exactly how much to ask so the insurer is forced to cover the demand.
Of course, victims are also typically contractually limited not to disclose insurance details to the attackers, and doing so risks losing any chance of the insurer covering the damages. This is why the hackers insist on these details to be shared privately.
Regardless of their offer, ransomware operators’ goal is to get paid and they would say anything to get the money. The reality is that they cannot be trusted.
Refusing to pay the ransom and reporting the incident to law enforcement along with having a consistent backup strategy are the only ways to fight this type of threat and bring it to an end.
The report from Varonis provides technical details on how HardBit 2.0 works starting from the initial stage and disabling security features to gaining persistence and deploying the encryption routine. The researchers have also shared indicators of compromise (IoCs) that help identify the threat.
Source: www.bleepingcomputer.com















