
HTML files remain one of the most popular attachments used in phishing attacks for the first four months of 2022, showing that the technique remains effective against antispam engines and works well on the victims themselves.
HTML (HyperText Markup Language) is a language that defines the meaning and structure of web content. HTML files are interactive content documents designed specifically for digital viewing within web browsers.
In phishing emails, HTML files are commonly used to redirect users to malicious sites, download files, or to even display phishing forms locally within the browser.
As HTML is not malicious, attachments tend not to be detected by email security products, thus doing a good landing in recipients’ inboxes.
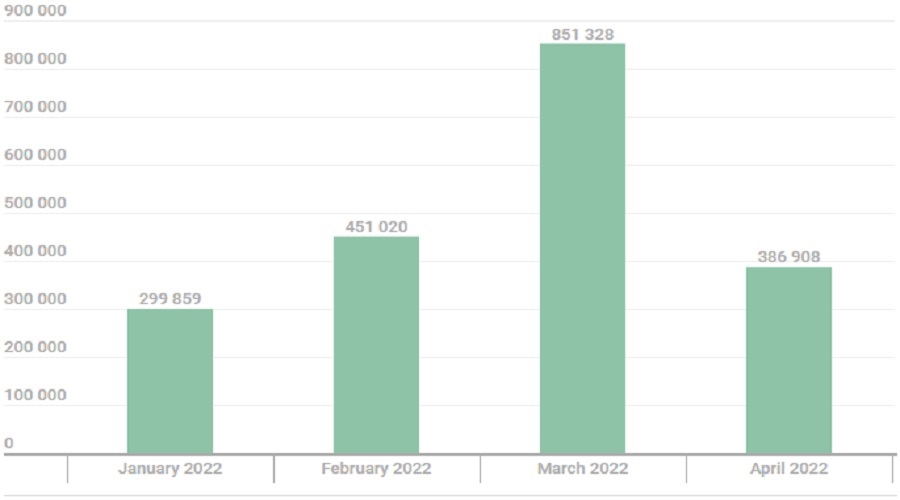
Statistical data from Kaspersky indicates that the trend of using HTML attachments in malicious emails is still going strong, as the security company detected 2 million emails of this kind targeting its customers in the first four months of the year.
The numbers culminated in March 2022, when Kaspersky’s telemetry data counted 851,000 detections, while a drop to 387,000 in April could be just a momentary shift.
How HTML evades detection
The phishing forms, redirection mechanisms, and data-stealing elements in HTML attachments are typically implemented using various methods, ranging from simple redirects to obfuscating JavaScript to hide phishing forms.
Attachments are base64 encoded when present in email messages, allowing secure email gateways and antivirus software to easily scan attachments for malicious URLs, scripts, or other behavior.
To evade detection, threat actors commonly use JavaScript in the HTML attachments that will be used to generate the malicious phishing form or redirect.
The use of JavaScript in HTML attachments to hide malicious URLs and behavior is called HTML smuggling and has become a very popular technique over the past few years.
To make it even harder to detect malicious scripts, threat actors obfuscate them using freely-available tools that can accept custom configuration for a unique, and thus less likely to be detected, result and thus evade detection.
For example, in November, we reported that threat actors used morse code in their HTML attachment to obfuscate a phishing form that the HTML attachment would display when opened.
Kaspersky notes that in some cases, the threat actors use encoding methods involving deprecated functions like the “unescape()”, which substitutes “%xx” character sequences in the string with their ASCII equivalents.
While this function has been replaced by decodeURI() and decodeURIComponent() today, most modern browsers still support it. Still, it might be ignored by security tools and antispam engines that focus more on current methods.
Conclusion
HTML attachment distribution was first seen spiking in 2019, but they remain a common technique in 2022 phishing campaigns, so they should be seen as red flags.
Remember, merely opening these files is often enough to have JavaScript run on your system, which may lead to automatic malware assembly on the disk and the bypassing of security software.
As the security software doesn’t detect an attachment as malicious, recipients may be more likely to open them and become infected.
Even if your email security solution doesn’t generate any warnings, you should always treat HTML attachments as highly suspicious.
Source: www.bleepingcomputer.com















