
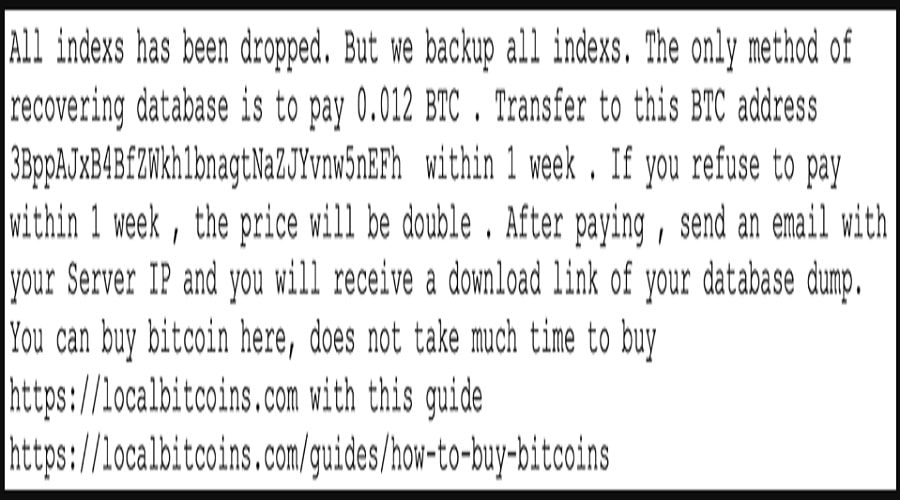
Hackers have targeted poorly secured Elasticsearch databases and replaced 450 indexes with ransom notes asking for $620 to restore contents, amounting to a total demand of $279,000.
The threat actors set a seven-day deadline for the payments and threaten to double the demand after that. If another week passes without getting paid, they say the victim would lose the indexes.
Those who pay the amount are promised a download link to their database dump that will supposedly help restore the data structure to its original form quickly.
This campaign was discovered by threat analysts at Secureworks, who identified more than 450 individual requests for ransom payment.
According to Secureworks, the threat actors use an automated script to parse unprotected databases, wipe their data, and add the ransom, so there doesn’t appear to be any manual engagement in this operation.
Campaign consequences
This campaign is not new, and we have seen similar opportunistic attacks numerous times before, and against other database management systems, too.
Restoring the database contents by paying the hackers is an unlikely scenario, as the practical and financial challenge for the attacker to store the data of so many databases is unfeasible.
Instead, the threat actors simply delete the contents of the unprotected database and leave a ransom note, hoping that the victim will believe their claims. So far, one of the Bitcoin wallet addresses seen in the ransom notes has received one payment.
However, for the data owners, if they don’t take regular backups, losing everything from such a wipe is more than likely to lead to significant financial damages.
Some of these databases support online services, so there’s always the risk of business disruption that could cost a lot more than the small amount demanded by the crooks.
Also, organizations should never exclude the possibility that the intruders steal the data to monetize it in various ways.
Elasticsearch security
Unfortunately, for as long as databases are exposed on the public face of the internet without securing them properly, these opportunistic attacks will continue to target them.
A recent report by Group-IB shows that over 100,000 Elasticsearch instances were found exposed on the web in 2021, accounting for about 30% of a total of 308,000 exposed databases in 2021.
According to the same report, it takes database admins an average of 170 days to realize they have made a configuration mistake, leaving plenty of time for malicious actors to perform attacks.
As Secureworks underlines, no database should be public-facing unless it’s essential for their role. Moreover, if remote access is required, admins should set up multi-factor authentication for authorized users and restrict access to relevant individuals only.
Organizations that outsource these services to cloud providers should ensure that the vendor’s security policies are compatible with their standards and that all data is adequately protected.
Source: www.bleepingcomputer.com














