
VMware has published security updates for the critical remote code execution vulnerability known as Spring4Shell, which impacts several of its cloud computing and virtualization products.
A list of VMware products affected by Spring4Shell is available in an adivsory from the company. Where a fix is not available, VMware released a workaround as a temporary solution.
At this time, it is critically important to follow the advice provided in the security bulletin, as Spring4Shell is an actively exploited vulnerability.
A flaw in a popular framework
Spring4Shell, officially tracked as CVE-2022-22965, is a remote code execution vulnerability in the Spring Core Java framework that can be exploited without authentication, having a severity score of 9.8 out of 10.
This means that any malicious actor with access to vulnerable applications can execute arbitrary commands and take complete control of a target system.
Due to the widespread deployment of the Spring Framework for Java app development, security analysts fear large scale attacks taking advantage of the Spring4Shell vulnerability.
To make matters worse, a working proof-of-concept (PoC) exploit was leaked on GitHub even before a security update had become available, raising the chances of malicious exploitation and “surprise” attacks.
Impact and remediation
The critical flaw impacts Spring MVC and Spring WebFlux apps running on JDK 9+. The exploit requires the app to run on Tomcat as a WAR deployment, although the exact limitations are still under investigation.
The fixed versions of the apps are:
- Spring Framework 5.3.18 and Spring Framework 5.2.20
- Spring Boot 2.5.12
- Spring Boot 2.6.6 (soon to be released)
VMWare has reviewed its product portfolio, and while the investigation is still continuing, the products below have already been determined as impacted:
- VMware Tanzu Application Service for VMs – versions 2.10 to 2.13
- VMware Tanzu Operations Manager – versions 2.8 to 2.9
- VMware Tanzu Kubernetes Grid Integrated Edition (TKGI) – versions 1.11 to 1.13
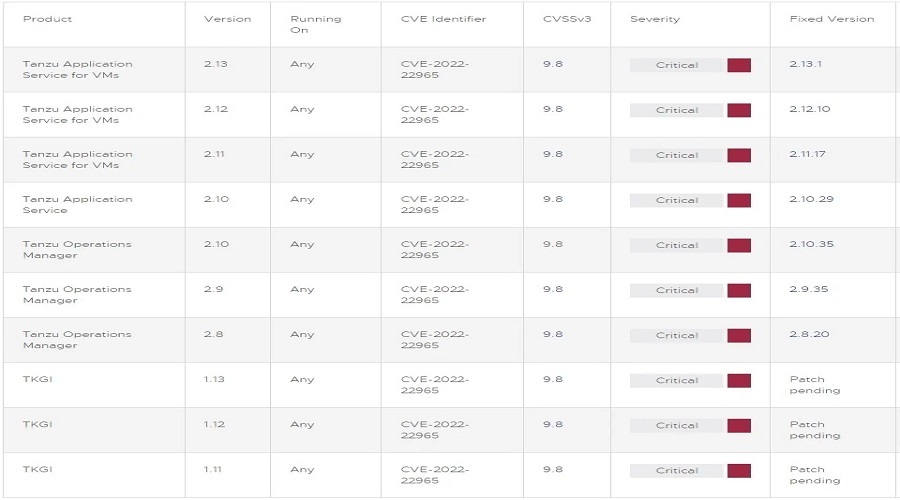
The vendor has already made available security updates for the first two products, covering multiple version branches with point releases, but a permanent fix for VMware Tanzu Kubernetes Grid Integrated Edition is still in the works.
For these deployments, VMWare has published workaround instructions designed to help administrators temporarily secure their systems until the patches are released.
One thing to note is that VMWare has found the Spring4Shell exploitation to be complex in TKGI, so the mitigation advice and upcoming security update are provided for maximum customer confidence and to avoid false positives.
Still, the provided official security recommendations should be followed without deviations and delay, to ensure that your deployments are safe from opportunist threat actors.
Source: www.bleepingcomputer.com














