A new DFSCoerce Windows NTLM relay attack has been discovered that uses MS-DFSNM, Microsoft’s Distributed File System, to completely take over a Windows domain.
Many organizations utilize Microsoft Active Directory Certificate Services, a public key infrastructure (PKI) service that is used to authenticate users, services, and devices on a Windows domain.
However, this service is vulnerable to NTLM relay attacks, which is when threat actors force, or coerce, a domain controller to authenticate against a malicious NTLM relay under an attacker’s control.
This malicious server would then relay, or forward, the authentication request to a domain’s Active Directory Certificate Services via HTTP and ultimately be granted a Kerberos ticket-granting ticket (TGT). This ticket allows the threat actors to assume the identity of any device on the network, including a domain controller.
Once they have impersonated a domain controller, they will have elevated privileges allowing the attacker to take over the domain and run any command.
To coerce a remote server to authenticate against a malicious NTLM relay, threat actors could use various methods, including the MS-RPRN, MS-EFSRPC (PetitPotam), and MS-FSRVP protocols.
While Microsoft has patched some of these protocols to prevent unauthenticated coercion, bypasses are commonly found that allows the protocols to continue to be abused.
A new MS-DFSNM NTLM Relay attack
This week, security researcher Filip Dragovic released a proof-of-concept script for a new NTLM relay attack called ‘DFSCoerce‘ that uses Microsoft’s Distributed File System (MS-DFSNM) protocol to relay authentication against an arbitrary server.
The DFSCoerce script is based on the PetitPotam exploit, but instead of using MS-EFSRPC, it uses MS-DFSNM, a protocol that allows the Windows Distributed File System (DFS) to be managed over an RPC interface.
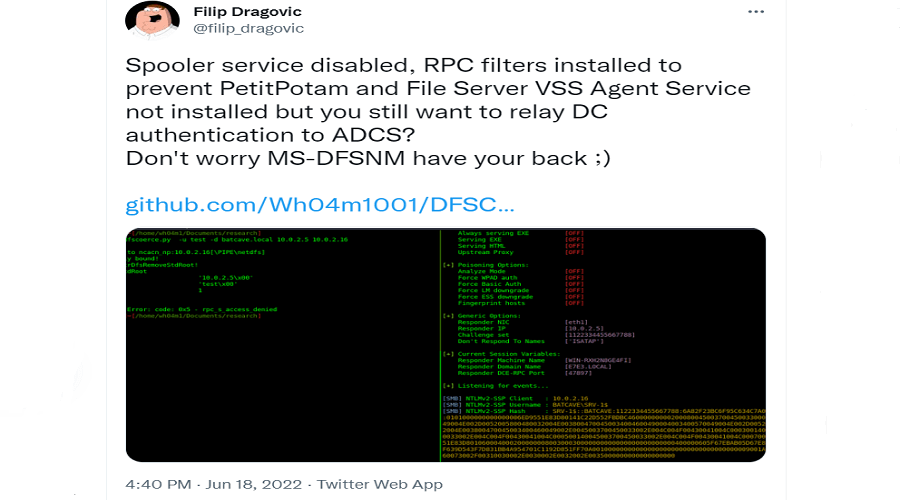
Security researchers who have tested the new NTLM relay attack have told BleepingComputer that it easily allows a user with limited access to a Windows domain to become a domain admin.
Researchers tell BleepingComputer that the best way to prevent these types of attacks is to follow Microsoft’s advisory on mitigating the PetitPotam NTLM relay attack.
These mitigations include disabling NTLM on domain controllers and enabling Extended Protection for Authentication and signing features, such as SMB signing, to protect Windows credentials.
Other mitigation methods include using the Windows’ built-in RPC Filters or RPC Firewall to prevent servers from being coerced via the MS-DFSNM protocol.
However, it is not known at this time whether blocking the DFS RPC connection would cause issues on a network.
BleepingComputer contacted Microsoft to learn if they plan on patching this new vector and will update the article with their response.
Source: www.bleepingcomputer.com