Many businesses will fail to see the benefits of their zero-trust efforts over the next few years, while legislation around…
Blog
Small businesses are just as at risk from cyber security threats as large enterprises. A common misconception for small businesses…
Social media has become an essential part of the business strategies of modern organizations. An active social media presence can…
Banking trojans are among the most insidious threats to both cybersecurity and personal financial security—and attacks are becoming more common….
With the surge in social media and online dating over the last decade, catfishing has become more common than ever….
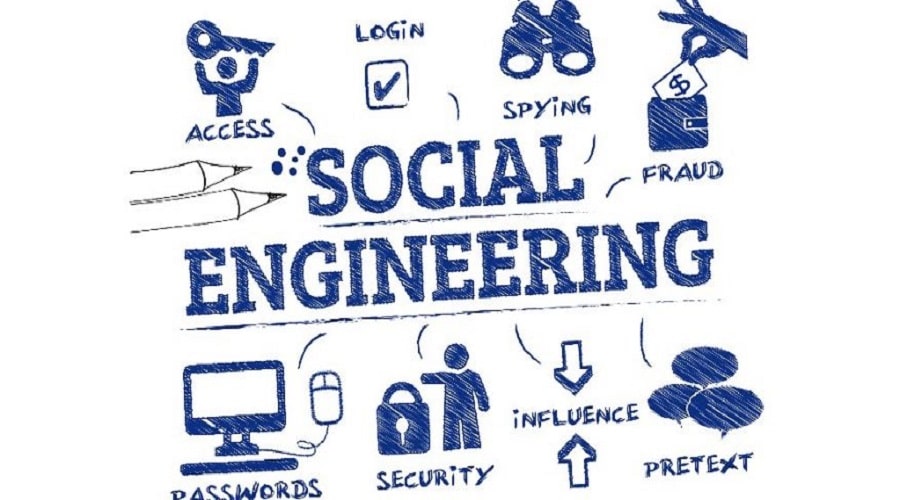
What is social engineering? Social engineering is an attack vector that relies heavily on human interaction and often involves manipulating people into…
iPhones are thought to be more secure than other smartphones. Anyway, hackers are getting more creative, and it’s time to…
Cybersecurity doesn’t have to be complicated. You can easily protect your Mac and your most sensitive data in a few simple…
We all know we shouldn’t download anything from sketchy links or websites, but sometimes even trustworthy app stores can be…
A computer worm is a type of malware that spreads copies of itself from computer to computer. A worm can…